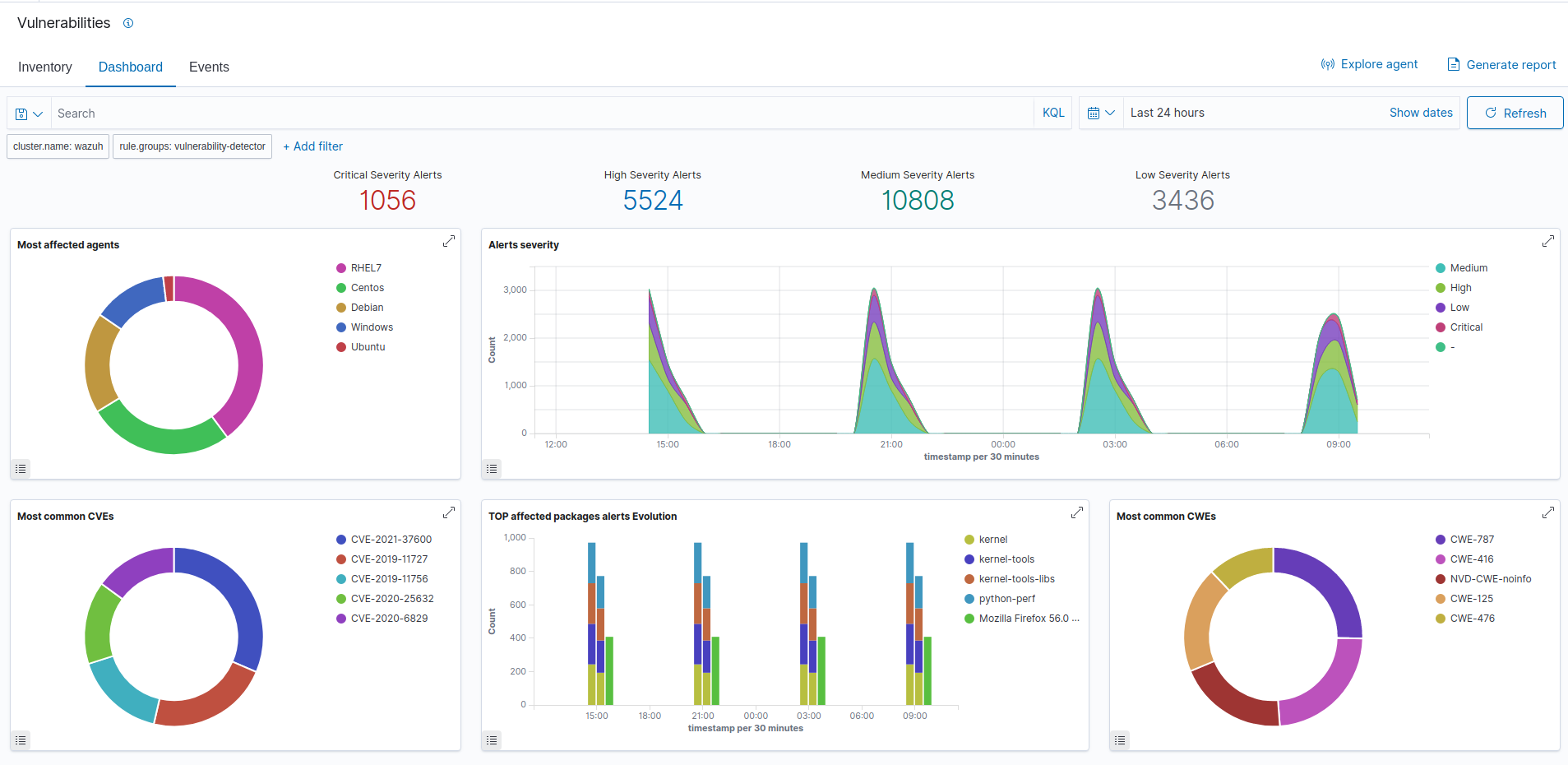
By the Numbers
Cyber threats are a harsh reality. It’s not a matter of “if” you’ll be attacked, but rather “when”. The stakes are high, don’t wait for an attack to happen. Our endpoint monitoring solutions empower you to take a proactive stance against cyber threats, detecting and responding to potential security breaches in real-time.
Manage Security and Response
Recognize
______________________________________
Comprehensive Oversight
Collaborates with your current technology setup to identify and characterize assets, as well as gather data and security event observations from various origins.
24×7 Monitoring
Our 24/7 monitoring service provides continuous surveillance of your facility’s security systems, ensuring that potential threats are detected and responded to in real-time.
Advanced Threats
Capture advanced threats overlooked by other methods with a platform that analyzes extensive security data and a seasoned team proficient in identifying.
React
______________________________________
Automated Alerting
We handle the investigation of suspicious activities, relieving you from alert fatigue and eliminating wasted time on probing false positives.
Incident Response
Our MDR service provides swift incident response capabilities, ensuring that security incidents are quickly identified, contained, and eradicated.
Containment Strategies
Our team develops customized containment strategies to minimize the impact of security incidents. This could include quarantining systems and networks.
Recover
______________________________________
Incident Eradication
In the event of a security incident, our MDR service helps eradicate the threat, ensuring that the root cause is identified, documented, and eliminated.
System Restoration
We provide system restoration services, getting your systems and networks back online quickly and securely.
Post-Incident Remediation
Our team conducts post-incident analysis, identifying areas for improvement and providing recommendations to prevent similar incidents in the future. We also take action against the attackers through governing authorities.
Advantages of an SIEM

Log Collection & Analysis
Our SIEM solution collects and analyzes security event logs from various sources, providing real-time insights into potential security threats. This enables swift detection and response to security incidents.

Advanced Correlation & Analytics
Our SIEM’s advanced correlation and analytics capabilities identify complex patterns and relationships between security events, enabling the detection of sophisticated threats that may evade traditional security controls.

Automated Alerting & Notification
Our SIEM solution provides automated alerting and notification capabilities, ensuring that security teams are promptly informed of potential security incidents and can respond swiftly to minimize damage.

Incident Response
Our SIEM’s incident response and case management features enable security teams to efficiently manage and track security incidents from detection to resolution, reducing mean time to detect (MTTD) and respond to security incidents.

Compliance Reporting & Auditing
Our SIEM solution provides compliance reporting and audit trail capabilities, enabling organizations to meet regulatory requirements and maintain a comprehensive record of security events and incident responses.

Threat Intelligence
Our SIEM integrates with threat intelligence feeds, providing security teams with real-time insights into emerging threats and enabling proactive measures to prevent potential security incidents.
Benefits of Open Advantage as Your Provider
Defend against cyber threats
Gain talented security engineers
Have an all-rounded partner
Gain More From Advantage Security
Don’t wait until it’s too late. Take charge of your security now by implementing robust, proactive measures. Safeguard your business, empower your team, and ensure peace of mind.
See it in Action
Want to see how our MDR service can help you recognize, react, and recover from security incidents? Our demo provides a comprehensive overview of our capabilities and showcases how we can help you strengthen your organization’s security posture and minimize the risk of security breaches.